Managing Critical Risk Vendors - Risk reviews, frequency, and key questions
Organizations outsource critical functions like technology and security solutions. The benefits of outsourcing are attractive. However, there are also inherent risks involved with outsourced services.

Risks associated with vendors who support an organization's technology and or/ security solutions include cyber-attacks, Wi-Fi attacks, DDoS attacks, third-party attacks and more. There are also possibilities of a data breach. Such risks can damage the organization's reputation and cause financial loss.
- The Regulatory authorities hold the organizations responsible for vendors' performance. Appropriate controls and discipline must be administered.
- Acquiring good knowledge about vendor risk management can help you exercise due diligence.
- By gaining knowledge of the vendor risk management, you avoid staking the organization's well-being and financial stability on a vendor.
This article provides instruction regarding the basic risk management components
Vendor Classification
The first step is to identify who your critical vendors are by using a risk-based approach. The vendor classification will help you determine the level of your oversight activity. Following attributes are classification indicators:
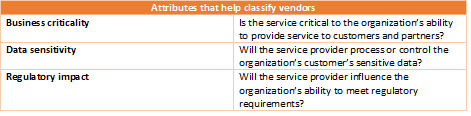
On classifying the above, add tiers according to their risk levels
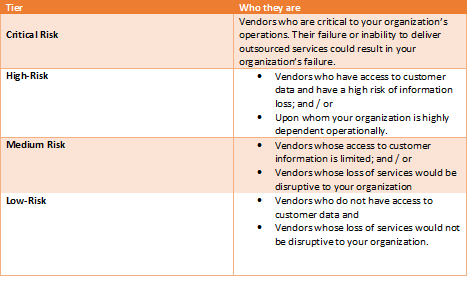
For ease of consumption, this article discusses the risk management components of a critical vendor who handles a core business function, or will be interacting with your customers.
Risk reviews are critical before enrolling the vendor on your supplier list and when the vendor is on board. Ongoing risk reviews ensure that the vendor maintains quality standards without causing any risk to the organization, investors or customers.
- Qualifying: Risk assessment in the Pre-contract stage, exercising due-diligence
- Is the vendor accurate with his response?
- Has he responded in a timely manner?
- Has he provided the documents you requested in a timely manner?
- The vendor does not provide processes for protection of confidential data
- Does not perform risk assessments internally
- Does not have a formal security policy
- Does not perform security checks across all functionalities
- Does not have a disaster recovery plan
- Engagement
- Perform ongoing risk reviews
- The vendor whose business exists for less than 3 years
- Items discovered in the last review need to be reviewed
- Vendor files bankruptcy
- Vendor layoffs
- Lawsuits that include the vendor
- Negative publicity concerning the vendor
- Lowered ratings by agencies (BBB, Fitch, S&P, Moody's)
- Increased vendor incidents or non-resolution of vendor incidents
- Key Risk areas to focus on:
- Handling of incident security
- Environmental security
- Organizational security
- Human Resource (HR) security
- Pandemic readiness
- Disaster recovery
- Handling data (hard and soft copy)
- Customer interaction processes
- Physical security
- Asset management
- Communication
- Access controls
- Key risk review questions - Tweak them to meet your specific needs
- Have milestones been met?
- Are deliveries fulfilled adequately and on time?
- Has quality matched expectations?
- Have costs been controlled in line with agreements?
- Is compliance clear and consistent?
- Has anything changed to threaten the vendor's business viability or stability?
- Has the vendor implemented AAA (Authentication, Authorization, and Accounting) for all users?
- Does the vendor Perform background checks for individuals handling confidential information?
- Does the vendor have termination or job transfer procedures that immediately protect unauthorized access to information?
- Does the vendor have customer support with escalation procedures?
- Does the vendor have documented change control processes?
- Does the vendor require contractors, subcontractors, vendors, outsourcing ventures, or other external third-party contracts to comply with policies and customer agreements?
- Does the vendor maintain a routine user Information Security awareness program?
- Does the vendor have a formal routine Information Security risk management program for risk assessments and risk management?
- Does the vendor have the following policies, standards, and procedures? Are documents ready available?
- Formal written Information Security Policies.
- Copies of the Information Security Policies.
- Results of a third-party external Information Security assessment conducted within the past 2 years (SAS-70, pen. test, vulnerability assess. etc.).
- Incident response procedures.
- o A policy that protects client information against unauthorized access; whether stored, printed, spoken or transmitted.
- A policy that prohibits the sharing of individual accounts and passwords.
- A policy that implements the following Information Security concepts: need to know, least privilege and checks and balances.
- A policy that implements federal and provincial regulatory requirements
- Access control - Does the vendor
- Immediately remove, or modify access, when personnel terminate, transfer, or change job functions?
- Achieve individual accountability by assigning unique IDs and prohibiting password sharing?
- Ensure that critical data, or systems, are accessible by at least two trusted and authorized individuals, in order to limit having a single point of service failure?
- Ensure that users have the authority to only read or modify those programs, or data, which are needed to perform their duties?
Introduce risk reviews to vendors during the Request for Proposal (RFP) process by embedding it inside the RFP if feasible in your current RFP process. At this point, monitor the vendor closely to determine future performance.
Warning signs that could remove a vendor from consideration:
Contracts include a statement of work, delivery date, payment schedule, and information security requirements
It is recommended that risk review for critical risk and high risk vendors be performed Quarterly/semi-annually. This is because of the level of risk involved. Some indicators that may call for more frequent risk reviews include:
Experience the unique opportunity to develop critical risk management skills to apply immediately upon returning to the office by attending the seminar 'Critical Vendor Risk Management'. In this fast-paced, highly interactive workshop attendees will develop a risk profile and risk management strategy using one of their own current or future vendors of choice.
The speakers are Rayleen M Pirnie, and Karen L Garrett. Rayleen's educational programs provide real-world, actionable information for financial institutions and businesses on topics ranging from payments risk management to information security. She authors payments risk and fraud blogs geared toward helping organizations recognize threats and protect themselves from loss. Karen L Garrett advises financial services businesses on payments, third party risk management, regulatory and operations matters, product development, compliance, M&A and other legal issues. Karen represents financial companies in connection with licensing applications and enforcement orders.






